identity resolution and risk levels
confirming the real-world identity of an individual
by Jem Shaw
Summary:
- Three million cases of identity theft and fraud, worth $1.48 billion, were reported in 2018, which is an exponential increase from $406 million in 2017.
- Identity Resolution and selection of attributes, as per the complexity, is crucial in allowing determination of an individual’s identity.
- The entire Financial Market Infrastructure (FMI) is in desperate need of an optimum balance between operational cost, customer onboarding time and risk management.
- Knowledge-based authentication (KBA) is just not enough!
Banks, financial institutions and customers are continually falling prey to the increasing problem of identity theft, falsification and duplication of records, thereby losing profits and facing customer disappointment. The identity authentication systems are filled with accidental errors or deliberate frauds. Before allowing for the resolution to a single identity, it has to be analyzed from different data sets, across various mediums.
So What is Identity Resolution?
Identity resolution is the process by which the identity of a customer is searched and analysed between different data sets across multiple databases and mediums and compiling a unified view into a single profile. Through identity resolution, banks and financial institutions get a comprehensive summary of a particular individual’s or company’s identity.
Why Do You Need an Identity Resolution Report?
An identity resolution report is evidence of the uniquely distinguished identity of a particular individual within a particular context. It acts as a confirmation that the document and data provided by the individual are associated with a unique identity.
The biggest problem experienced by any client in the financial sector is — tedious onboarding time. According to a Reuters 2017 survey, 12% of clients have switched to a different FI due to the current KYC process. [1] Considering the compliance and regulations, it is imperative to keep the process as stringent as possible, if possible, to make it more effective. However, there still exists the need for a more convenient method for the customers as well as FIs to overcome the tediousness of the entire process since faster customer onboarding time is a major determinant for every FIs’ success.
And the first step in this process is Identity Resolution.
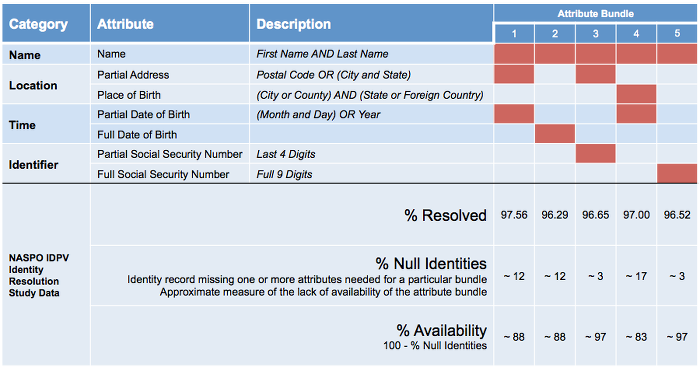
Categorisation of the attributes for Identity resolution in KYC
An individual’s identity is based on the commonly exercised set of attributes. The categories include:
- Name
- Location
- Time
- Multiple Unique Identifiers
These dimensions can be further segmented into the following attributes:
- Name: First Name And Last Name
- Temporary Address: Postal Code, or City and State
- Place Of Birth: City or County, and State or Foreign Country
- Date of Birth: Month and Day or Year
- Full Date of Birth
- Partial Social Security Number: Last 4 Digits
- Full Social Security Number: Last 9 Digits
The common documents required to perform a KYC check on a customer include, but are not limited to, a Voter ID card, Social Security Number, Government Tax Return Reports, Bank Statements, Address Proof, and Social Demographic Identity.
How Does Identity Resolution Work?
To avail the services of a bank or FI, the bank requests the customer to provide their Personal Identifiable Information (PII) for identity verification. Generally, the bank outsources this process to a Credential Service Provider (CSP) to provide electronic credentials or tokens to the subscriber for registration accessibility and recovery.
Meanwhile, a Registration Authority (RA) ensures that the documents submitted by an entity meet all the requirements of an identity resolution attributes as per the specific requirement of the FIs.
This is done by generating a report of the Identity Assurance Level. The identity of a client is analysed across multiple sources by the RA who vouch for the subscriber/client and provide a level of assurance for assisting the FIs to assess the associated risk factor. Basically, post report, it’s the MLRO’s (Money Laundering Reporting Officer) call to move forward with the client’s onboarding (in the current system where manual customer onboarding is being used instead of automated identity verification).
Importance of Components of Attribute Selections
The characteristics of the attributes for defining the uniqueness of a customer’s identity is based on the following factors which depend on the use case of the identity resolution required by the verifying entity:
1. Effectiveness
Whether the attributes are effective in distinguishing the customer’s identity
2. Sensitivity
If the customer is hesitant to share his/her attributes as it may have some repercussions
3. Accessibility
Is the customer able to access the source that can verify his/her claimed attributes?
4. Permanence
Are the attributes independent of the time variable?
5. Unavoidability
Is it mandatory for the customer to submit a specific set of attributes? Here we are talking from a very wide perspective and the requirement may vary significantly, however, this gives a general idea about factors affecting identity resolution.
So what about KBA and how secure is it?
Is your authentication process smart and secure enough to protect your personally identifiable information? Does anyone else know about the Knowledge-based Authentication (KBA) questions?
“What is your mother’s maiden name?
What is your first pet’s name or your favorite destination?”
Well, it’s in fact quite simple! A quick social media search by an attacker can easily reveal this information to form an effective digital profile capable of authenticating your identity. [4]
"But single-factor authentication offers quick authentication, and gives access."
Yes sure, but at what and, for FI’s, at whose cost? FIs not only have to make sure that the monetary aspects are in check but also that customer data are secured. And this is why the industry is migrating to at least, two-factor authentication (2FA) and for better security, multi-factor authentication (MFA).
OTP, Biometric verification, Digital Signature, and (MFA) in a blockchain-based system like biz.Clarency can be the ultimate solution. Basically, the strength of authentication required is determined by the level of risk assessment. SMS and call interception by hackers are common security risks associated with 2FA, so, to form another layer of security, multi-factor authentication could be the key. Identity assurance and authentication assurance are equally important.
Assurance Levels For Risk assessment
Authentication factors increase with the level of assurance required, therefore it has become critically important for CSP and FIs to perform strict and higher-level risk assurance across AML and CFT databases.
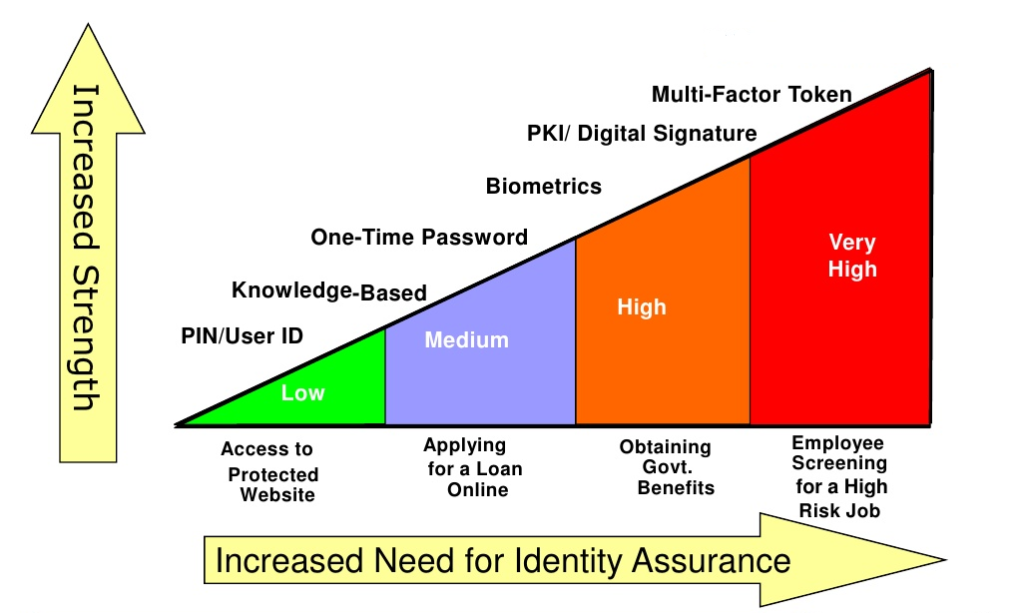
The assurance level of an identity resolution report are:
1. Identity Assurance Level (IAL)
IAL 1
The customer is self-assured at this level. The customer onboarding time is very quick. No additional information is required to assign a real-world identity. No specific methods are performed across different databases and channels.
Use Case
During a signup process to a social media website, you will be asked to provide general information and get enrolled very quickly. No document of identity will be asked for verifying your real-world identity.
IAL 2
The customer is required to provide the documents so that it can be used to authenticate through remote or physically-present identity proofing and assign them to a claimed real-world identity.
Use Case
To sign up into some mobile payment wallets, you will be asked for some documents and remotely asked to verify your real-world identity.
IAL 3
The customer and all the documents are rigorously authenticated across every data set, channel, devices, and mediums. In the presence of a trained and authorised representative, the identity of the customer will be authenticated in real-time.
Use Case
When enrolling into a bank or any financial services, the customer will be asked to provide all your documents. A trained representative will verify the identity of the customer and rigorous checks will be performed on different channels and databases.
2. Authenticator Assurance Level (AAL)
AAL 1
A customer will be required to provide a single-factor authentication to verify the identity.
Use Case
The customer is asked to sign into their accounts with a password that acts as a single-factor of verification.
AAL 2
This is a high-confidence process that requires a two-factor encrypted authentication key from the customer to verify the identity of the customer.
Use Case
As two-factor authentication, the customer will be asked to verify their identity by providing a password and are required to provide a biometric verification or secured one-time-password (OTP) that is sent on their email, voice mail or mobile devices.
AAL 3
This is a very high confidence and rigorous process. This authentication is based on the possession of a key through a cryptographic key.
Use Case
Banks and FIs are using blockchain technology to provide a highly-unique cryptographic key to the customer for identity authentication and verification. The security of these technologies makes this process very hard to bypass for identity thieves.
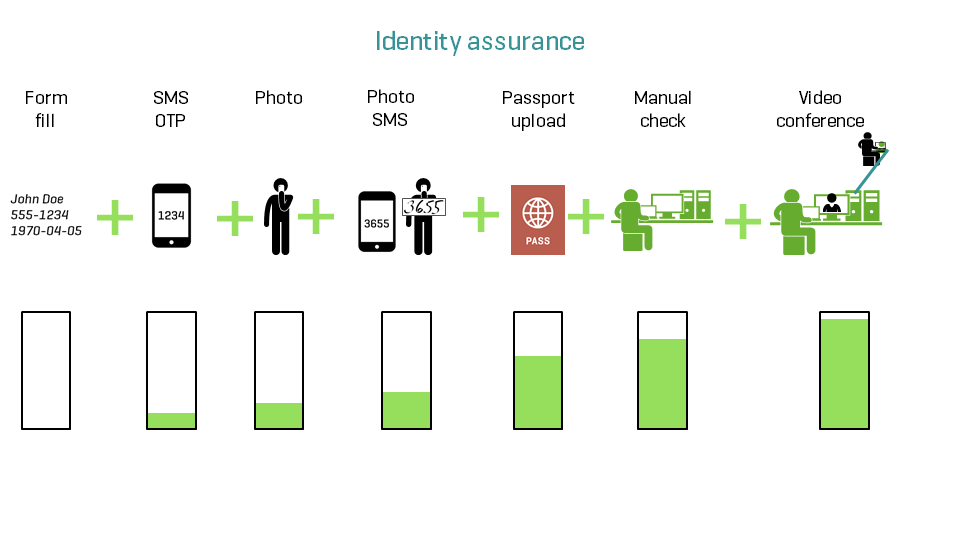
IAL 3 and AAL 3 play a huge factor for identity resolution and to block all the channels of identity theft. [5] For banks and FIs, maintaining the standards and accuracy of validation and authentication is a necessity and it is the responsibility of Fintech solution providers to make that happen.
So the final question that an organization, in fact, any responsible individual should ask is — which level of assurance is required? At present, the industry leaders do not have (or maybe don’t want to implement) a solution that will strike a balance between time, cost, and security but the decision-makers at a few firms, for example Choice International, are going forward with it with highly encouraging results.
Many promising solutions and ideas are still in the development phase, and a real-world-applicable one-step solution is coming ever closer. Until then, a more secure identity proofing is the need of the hour, and information from digital sources is our best shot. However, should only a limited number of data from web footprints be considered as a legitimate KYC? If data has to be mined, shouldn’t data sovereignty be a norm, or, in fact, a law? And will the solutions be effective and compliant with the financial regulations?
Some questions are yet to be answered. Yes, there are problems, there are complications but there is always an answer. The solution may already be here, so the real question is:is the world ready to accept it?
