who am I speaking to please?
the increasing importance of identity verification
by Jem Shaw
Summary:
- FIs have been fined $26 billion in the last decade for failing to comply with AML compliance laws amp; regulations
- The FMI industry is experiencing high customer acquisition cost with low revenue growth and reduced customer acquisition
- Financial terrorism and identity theft have become rampant necessitating higher investment in data security and identity verification
- Huge investment is being made to balance positive verification against customer onboarding experience
- New startups have entered the market with advanced technologies and better verification methods like e-ID Mobile ID KBA amp; MFA and gesture-based facial and speech recognition
Businesses, and particularly financial institutions, are facing a massive increase in customer acquisition cost and stricter global compliance regulations. Organisations with traditional verification systems, and even those with more advanced digital identity verification methods, have experienced hefty fines for violating AML and compliance laws. On more than a few occasions the situation has escalated to considerable damage to brand image and even temporary or permanent shutdown. The problem is widely recognised and hotly debated, yet still no product has emerged to solve it.
In an expanding international market, why are financial institutions losing customers and revenue?
As the need for enhanced diligence increases, so does the complexity of the onboarding process, leading to delays and a worsening customer experience. This actually favours organisations with poorer security procedures, as customers migrate to less obstructive onboarding. And as well as helping wrongdoers to hide in the "noise" generated by bona-fide customers moving to these organisations, this also inevitably leads to more compliance violations and service interruptions. As crime moves more and more into the digital space, so phishing, hacking and identity theft becomes more widespread. We repeatedly read of data breaches in major corporations and regulatory penalties continue to rise.
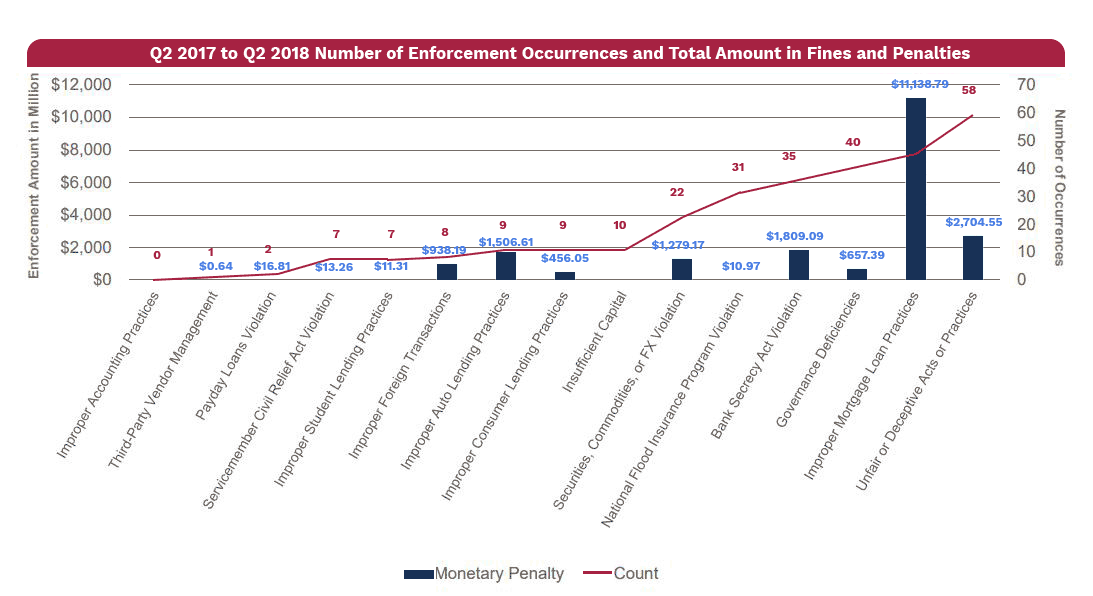
Fines as high as $26 billion have been levied on financial institutions in the last decade for failure to comply with identity verification and AML/CFT laws. But the poor customer experience resulting from even inefficient counter measures may hurt the FIs still more We've become accustomed to the immediacy of the Internet. and so are less willing to accept delay - especially when those delays can easily extend from days to weeks. Manually intensive diligence procedures tend to hide from the end customer the fact that their case is being worked on at all, albeit slowly. But even this anachronistically extended process might be accepted if it actually protected the parties concerned. The graph above makes it startlingly clear that this isn't the case.
Data sharing across social media and buy-online companies means that the information required to pass the traditional GDPR questions such as home address date of birth and mother's maiden name are easily discoverable. As identity fraud becomes easier, so due diligence processes must become more intense. Delay and cost spiral upwards while customer experience nose-dives.
But does this shared information offer an opportunity to make diligence more multi-dimensional? We're already seeing social media, press coverage, location data and other elements of the so-called "digital footprint" being used in AML/ATF procedures. But the gathering of such diversely located and distributed data is a lengthy process that further impacts customer experience. What's needed is a system that can automate the process of aggregating and correlating data from widespread sources to present a single easily analysed view.
Types of Identity Verification
Before we move further with exploring this unified approach, it's worth reviewing the main "flavours" of identity verfication
Electronic Identity Verification (eIDV)
The widespread deployment of public and private databases has enabled identities to be interrogated electronically. Credit bureaux, police records, vehicle address, and a host of other records, can be explored and - in the case of more advanced systems - cross-referenced. While a utility bill and driving licence - often all that's required to open various accounts - can be relatively easy to forge it's extremely difficult to falsify dispersed information held by completely independent bodies. EIDV also exposes frauds such as use of a deceased person's social security number.
The most limiting disadvantage of eIDV is in its coverage. In emerging regions, 20% or more of the population may be unlisted .
Mobile ID Verification (M-ID)
The ubiquity of mobile devices has allowed an additional layer of validation to be overlaid upon eIDV. Mobile companies have access to highly detailed customer information, including geo-location and verified physical and e-mail addresses. An increasing number of mobile devices now offer facial recognition and fingerprint scanning, which not only protect the user's security, but also provide positive identification of customers.
Older devices, network coverage and availability in poor societies are an obstacle that hopefully will reduce over time.
Some organisations also need to re-examine their methods of implementing M-ID. For example, sending a validation code back to the device attempting to make a transaction offers no protection if that device has been stolen.
Document Verification (DV)
The old-fashioned verification method of examining statutory documents has evolved into more revealing electronic inspection techniques. While humans can be relatively easily fooled by a passable forgery, machines - especially those with AI capabilities - can spot false documents rapidly and reliably. The more powerful verification systems can detect covert verification errors, such as internal checksums and specialised fonts, while almost concurrently checking for previous occurrences of an individual's photo under differing identities or appearance in AML or CFT databases.
DV is a highly promising and powerful verification tool It's a relatively complex process though, which can cause delays in delivering report results. More advanced systems such as biz.Clarency minimise or eradicate this shortcoming by background processing while other KYC requirements are being entered.
Video Identification (VI)
Early facial recognition techniques could be fooled by holding up a photograph of an authorised person. While most (though not all) have moved on to a more robust model, this shortcoming has given birth to an improved technique using motion video. The system analyses random gestures and speech patterns to make a positive identification. It may reference sources like AML/CFT databases, or even social media to establish identity. VI thus works best when implemented as part of a multi-factor authentication regime.
Multi-Factor Authentication (MFA)
Every method of identity verification has shortcomings, be it an inherent vulnerability in the system itself, or incomplete penetration of the technology that facilitates it. The latterconsideration also highlights the fact that not all of the factors may be available in all of the cases under inspection. It's therefore vital that any robust verification regime must use multiple approaches in order to reach a dependable risk decision.
The barriers here are time and expense. Executing multiple queries can necessitate an increasing number of service subscriptions. And potentially more expensive is the time of a risk office,r who may be required to repeat queries across a range of login security regimes. The results then need to be aggregated and compared - a time-consuming and error-prone task when result formats may differ considerably.
Conclusions
- Financial institutions need to up their game in ensuring the person they're speaking to is the person they think they're speaking to
- This has to be done with minimum impact on customer experience
- Technological advances need to be embraced to stay ahead of the fraud curve
- EDD costs need to be controlled - and ideally reduced - to allow more inclusive trade
- FIs should seek a technology-advanced service provider able to aggregate MFA information via single log-in and commercially viable pricing
